Security
Your ISP Potentially Knows EVERYTHING that you do through your Internet Connection
Q. Who knows more about your internet use then Facebook, Amazon or even your browser?
A. Your ISP and NOW they can collect and sell your internet usage information!
Q. How can you protect yourself?
A. Keep reading this blog!
Quietly last March, Senate Joint Resolution 34 repealed US broadband privacy regulations that had been in place through the FCC. What does this mean? It means that without your consent your ISP (the company that connects you to the internet) can collect your internet usage data and sell it.
As I write this the headlines are full of personal data leaks from Facebook, but I can’t help thinking this is peanuts compared to what might happen if profiles collected by a large ISP are stolen (or even sold) en masse.
The only thing Facebook knows about you (or perhaps your friends) is what you have done in Facebook or its related apps. Your ISP potentially knows EVERYTHING that you do through your internet connection including all of your browsing, all of your apps, phone calls, smart appliance usage, security camera information and every single packet of information that passes in and out.
You might say “But Tim, I only go to SSL protected websites, my ISP cannot see my data because it is encrypted”. Well it is true that if you use SSL protected websites, your ISP likely cannot see what you are doing at that website. But they do know where you are going, how often, when and how much data was passed. Thanks to the work during World War II by forgotten hero Gordon Welchman, ISPs or anyone else with mathematical prowess can make an amazingly comprehensive and accurate profile of you without ever knowing the content of a single message that you have sent.
One way that you can hide all of your activity from your ISP is to use one of the many VPN (Virtual Private Network) products that are on the market. By using a VPN you can hide ALL of your traffic from your ISP. Your traffic appears to be one single encrypted connection to your VPN provider. The problem with this approach is that now you have to find out if you can trust your VPN provider! VPN providers can promise a lot of things but in the end they might be even worse at protecting you than your ISP. Additionally, VPN connections can slow your internet throughput and any VPN that is reasonably trustworthy is going to be an added expense (NEVER use a free VPN service).
If you have the bandwidth, time to research your VPN provider and can spare the funds, a VPN may be an excellent way to improve privacy over your standard ISP. Remember that the principle advantage to using a VPN is that all traffic is encrypted and the principle disadvantage is that you have only moved who can watch your traffic from your ISP to your VPN vendor.
When it comes to security, especially information security, it seems all of our options are really mitigations -- a balance of give and take.
Another method to keep your ISP and anyone else from monitoring and tracking what you do through your internet connection is to use one of the Tor family of tools.
The Tor products are free and have an amazing history. The technology behind the Tor system was funded by the NSA (National Security Agency) to protect US spies and operatives. Due to what perhaps was a lack of foresight, the Tor tools were put into the public domain during development, and with the “cat out of the bag”, everyone can benefit from these security tools. If some current leading security experts are right, the NSA apparently regrets letting the TOR technology out because even they cannot monitor the traffic protected by these tools.
The Tor team is an open source group that makes and updates free products to protect your identity when you use the network, fundamentally making what you do on the internet anonymous.
Tor is used not only by regular folks to protect the identity of family members; it is also used by business to research competition, to keep business strategies confidential, and by whistleblowers so they can safely report. Tor products can be used by media and law enforcement to protect sources, investigations and intelligence. Like any powerful tool it can be used with both good and bad intentions and much of the regular media press that the Tor project receives is often about criminals using it to hide their identities.
The Tor tool kit is quite large but for this introductory blog we are just going to cover the two simplest and most common tools and how to use them.
The first tool we will look at is the Tor browser. This is a browser that you install on your operating system much like Internet Explorer, Chrome or Firefox. In fact, it is a modified version of Firefox. This tool provides a quick and easy way to start using Tor.
The second tool we look at is the Tails OS. Tails OS is a complete operating system with pre-installed applications designed from the ground up to be fully secure and anonymous. You don’t have to install Tails OS if all you want is a secure browser but having a fully secure operating system with pre-installed tools is very powerful should you decide to make the extra effort. Tails OS is a unix-like operating system but don’t let that scare you off --it has a simple installation and an intuitive GUI interface.
Option One. Tor Browser
Step one download and install the TOR version of the Firefox browser.
Go to www.torproject.org and click on “Download Tor”
Note the usage suggestions under “Want Tor to really work?”
Click the second “Download Tor” button’
Step two install the browser like you would any other application.
Step Three launch Tor browser.
If you have just installed Tor you should have the newest version, but always look at the first page anyway because that’s where you’ll be warned if your version needs updating to fix a security hole.
Click on the link “Test Tor Network Settings”
If everything is going well you will get a “Congratulations” message and it will tell you what your ‘fake’ IP address is. Often this spoofed IP address is from another country so don’t be surprised if some websites think you want the weather in Europe. If you want to roll the dice and take on another random fake identity click on the green onion icon at the TOP of the browser and choose “New Identity”.
You are now browsing the internet as an anonymous user! How cool is that?!
You can see what country you appear to be from by clicking on the green onion icon drop down menu at the top left.
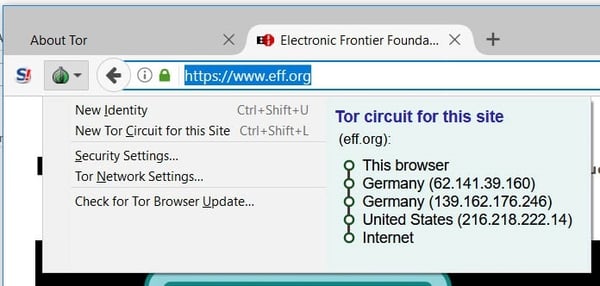
If you don’t like your connection you can “roll the dice” for a new connection by choosing “New Identity”.
Step Four (optional) Going full stealth.
With your current default settings you are now very well protected and for most websites you are now anonymous but there are some “evil” websites that use flaws in operating system configurations to expose your computers real IP address or MAC address. This still does not tell the website who you are but it could expose your location and the manufacturer of your computer.
To keep these “evil hacker” websites from trying to expose you, just turn the security settings of your Tor browser from “standard” to “safest”.
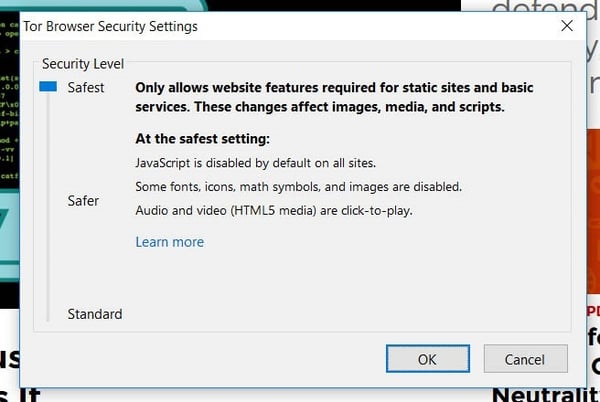
The downside to turning this option on is that you may lose some or all functionality from websites that use Java Script code.
The good news is that you can turn the “safest” setting on and off at will without restarting your browser.
Step Five Have some fun!
Spend some time browsing to some sites and see what changes when they don’t know who you are or where you are really located.
For instance Google may not function since your browser will not respond to its identity queries against your computer and may give you an error like “Our systems have detected unusual traffic from your computer network. Please try your request again later.” That might be because Google pays it bills by “tracking you” or more correctly analyzing your behavior and selling that data though Google analytics and other products. Instead try a search engine that does not track your usage like Duck Duck Go or Start Page (links to both are in the search field of your Tor Browser).
Try going to some news websites and see if the news you are presented with is different since they think you are from a different location or country.
If you are satisfied with your new found anonymity, skip over the next section and read the conclusion topic at the end of this blog for some further recommendations. If you would like to make all of the traffic from your computer anonymous, not just your browser, read on to Option Two.
Option Two. Tails OS
The Tor browser is easy to install and is a great tool. However, it is only making your internet browsing anonymous, not your instant messaging, email and other services or actions carried out on your computer.
The Tails OS offers both anonymity and amnesia. Anonymity means that our identity is hidden and amnesia means that no trace of activities done on the computer are retained.
What if you also wanted to leave no trace of any of your actions on your computer in the form of logs and temporary files from any program you run? Laptops are easily lost or stolen especially when you are traveling and if you have critical correspondence to protect you might want to consider the Tails OS. If you need to use other people’s computers but you don’t want to leave behind usage logs or install the Tor browser on the computer the Tails OS might be an easy all in one solution.
The Tails OS will require a bit more work to set up so you will need some technical experience or the time and will to work though the step by step instructions published on the Tails OS website. What you end up with is a very secure operating system that boots from a simple small USB drive. Everything you do on the computer booted from this thumb drive is both anonymous and no trace is left on the computer of your activities.
Tails OS is certainly not for everyone. If you are an international correspondent traveling in countries that censor articles or free speech or have a small company that can’t afford big IT security and encryption software to protect your new patents and processes, perhaps Tails OS is a solution for you. If you need to send some sort of whistleblowing evidence, anonymously report an ongoing crime, especially on a computer that may not be completely secure and free of malware, you might also consider Tails OS. However, for any anonymous browsing you want to do on a computer that is well patched and trusted, the Tor Browser should be all that you need.
Conclusion
The internet is a public network and like any public place we need to think about what actions we take in it. Even if the ISP privacy laws are reenacted, privacy is difficult to achieve on the internet unless you are a well-educated consumer. For companies and services like ISPs, browser developers, search engines and social media forums to be motivated to offer privacy protections, consumers need to be willing to pay for these features and/or switch to competitors that offer privacy protections.
Like any commodity, privacy protection tools and features become stronger and cheaper the more they are used and when more people use them.
One great place to learn about internet privacy, tools, current issues and how to make the internet world a better place for all of us I recommend you frequent the EFF (Electronic Frontier Foundation). https://www.eff.org/
Even with fully anonymous connections to the internet you can still be conned into accidently sharing important personal or financial information. To protect yourself from these cons, no matter what kind of connection to the internet or services you use, it is critical for you, your family and your fellow employees to be security-aware. Security Awareness classes are effective and inexpensive.
Further Reading:
BBC Two – Bletchley Park: Code-breaking’s Forgotten Genius
http://www.bbc.co.uk/programmes/b069gxz7
Development of TOR, BBC Horizon: Inside The Dark Web
http://www.bbc.com/news/technology-29032399
Electronic Frontier Foundation



