Written by Tim O'Connor - AKA "King The Silly Flashdrive"
 Your actions on social media could inadvertently result in a friend or family member losing their home or car. If you want to avoid this, please read this entire article.
Your actions on social media could inadvertently result in a friend or family member losing their home or car. If you want to avoid this, please read this entire article.
I keep seeing articles and advice telling people to beware of games or apps on social media or to be careful about what you share. However, most of the time these articles don’t actually educate you on how these hacks work. I think this results in the so-called “what the hell effect” so people just carry on sharing content, feeling helpless because they don’t know what is safe or not safe to share.
Let’s learn a popular hack!
If you have been following some of my articles you know I like to teach how con-games work and even how to practice them yourself. Social media con-games are just like most social engineering hacks --just more cons that have been around for a hundred years. They work because they look harmless and appeal to basic human desires or biases.
Knowing just a few dozen cons and how they work will give you protection from most exploits as social engineering cons typically have a great deal in common once you know what to look for.
Today I am going to explain a social media con-game that is understandably appealing to innocent bystanders. After you read this you will be “inoculated” against this con and perhaps you won’t join the yearly 16.7 million victims of identity theft.
What’s your elf name?
Have you ever seen a mentalist performer reveal personal information about a participant, information that the mentalist could never have known? Perhaps the mentalist knew that person’s dead relative’s name or astrological sign. This is done through a process called cold and warm reading. With cold and warm reading, mentalists (or con-artists) ask you for information indirectly which gives them enough clues to accurately guess something personal or private about you.
If they can even slightly distract you during this process you won’t even realize what information you have given away or how that information can be used.
We can see this technique easily with the “What is your ______ name” memes. When it is near the holidays, you might see the meme “What is your elf name?”, or when a new movie is out you might see “What is your Jedi name?” and so on. In these games, you take a piece of seemingly personal information about yourself (astrological sign, favorite pet, mother’s last name) and combine them to make a fun “name” related to the event. (See Example Illustration). The meme will often then ask you to post the name you have generated.
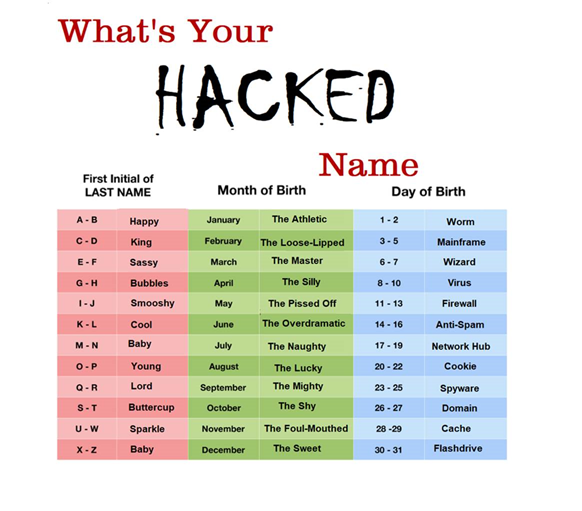 What just happened?
What just happened?
The result is that you have provided partial or complete information toward building a profile that will allow an evil hacker to clone your cell phone, take out loans in your name, case your physical property for theft or a hundred other crimes. Anyone able to see the responses to the meme can easily reverse the name to see your personal information.
You are likely hurting friends, family, and other employees more than yourself.
Russian evil hackers use the phrase “poleznyy durak” for people that they do NOT attack directly, because they do such a good job of sharing these hacks with their friends, family and coworkers. These hackers are smart enough not to jeopardize the trust of these people because their social channels are wide open to evil hackers, who can then bypass much of the security used by social media.
When you share these posts and your friends comment on them, this opens up “friends of friends” social media attacks, letting hackers peer into the accounts and information of people who try to keep their social media presence and information less public. When one or more of your friends shares this again, the chain grows and becomes a deep-rooted network of useful information.
Talented evil hackers will try to go after these innocent bystanders rather than those “share-aholics” because they want to cover their tracks, as well as not cut off their best promotors.
Now you know how to protect yourself, family, friends, and coworkers.
Some of these memes are indeed harmless fun. “What was the last book you read?” or “What is the color of the closest object to your right?” are examples of games that don’t provide any serious information loss. But if we are asked about, say, a pet’s name, what is the harm? Unfortunately, a large number of people choose weak passwords related to their everyday life. If you know the names of someone’s pets, favorite actors, children or other personal things, “cold reading” their password will become much easier. Knowing what street you grew up on may seem harmless but that gives clues to the security questions that might be asked to change the password to your online banking account!
“Personality quizzes” are more than just a graphic meme and thus, can be even more valuable to evil hackers. However, as they are more complex, they would take more time to explain. As you would expect, they release even more personal information.
If you have someone you care about, you might ask them to read this article or the links I’ve provided below. More likely, it will be easier to just explain to your friends and family that these quizzes are an old “magician’s trick” to get you to share information and that doing so can get you hacked.
I would recommend that if these kinds of quizzes have been shared in the past by one of your accounts, you should delete them.
If a friend shares one of these in the future, send them an instant message explaining the security risk. I don’t recommend posting directly on their feed because it may embarrass them and make them defensive.
Security Awareness programs at work should include information like this, since knowledge empowers employees and protects the organization. If your security awareness program at work is missing this information, please make the program designers aware.
Have fun.
Not everything on social media is doom and gloom! You might even try turning the tables on the hackers. Make sure that you and the family always put in FALSE information every time you see such a quiz! This will chew up the evil hacker’s resources and it’s fun to do!
Referenced links:
1. “What the hell effect” is really a thing! https://www.psychologytoday.com/us/blog/pressure-proof/201701/how-the-what-the-hell-effect-impacts-your-willpower
2. https://blog.cadre.net/how-to-legally-practice-social-engineering
4. Cell phone exploit blog: https://blog.cadre.net/tech-security-insights/how-to-avoid-the-4-top-security-cons-in-2020
- Russian Social Media Manipulation blog: https://blog.cadre.net/if-you-think-iranian-and-russian-disinformation-memes-are-designed-to-changes-peoples-minds-and-opinions-you-might-already-be-deceived







