Security
Taking Over Master Membership and Securing VRRP
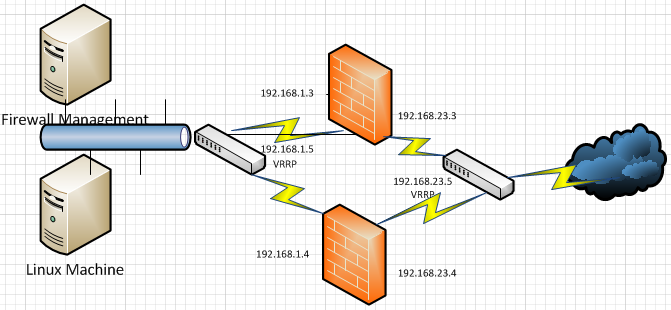
Part 1 (No Firewall Module)
Instructions for setup are in the link above. You must install two firewalls and configure VRRP on both of them to act as a cluster. The first part of this exercise is pure VRRP with no firewall module running.
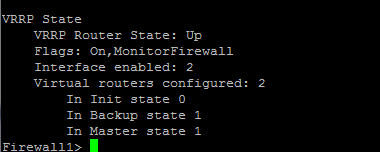
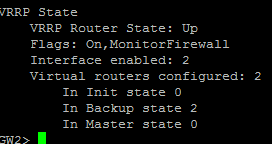
When configured properly, you should have interfaces in Master on one device and interfaces in Backup on the other device.
Once the Loki machine is on the same network and the attack is first launched, it will see what physical machine is presenting which virtual IP on that network.
Once Loki has identified the machines, you have the ability to take over that IP address.
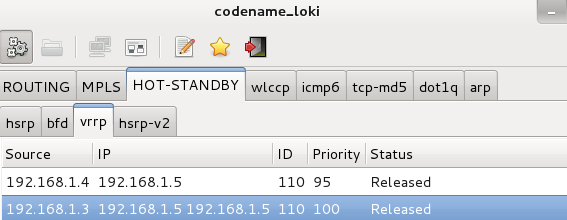
The screenshot above was from when I was making the cluster flap back and forth so it captured both physical IP addresses of the members.
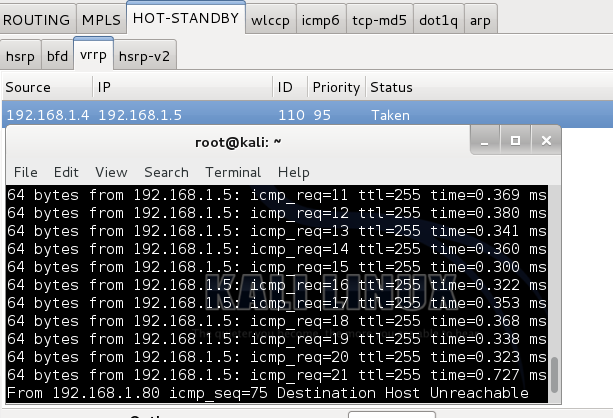
Once I launched the attack on the master member, you can see the virtual IP no longer replies. Notice the status has changed to “Taken” from “Released."
Part 2 (Firewall Module Running)
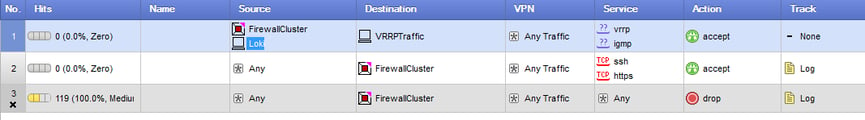
Firewall policy is as such, with Antispoofing enabled on the gateways.
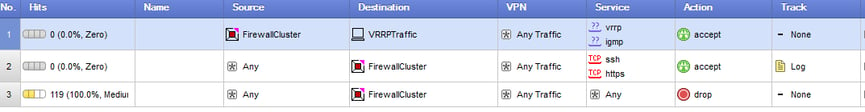
With the configuration above, I could not take master membership in the cluster due to the security rules for the VRRP. A zdebug showed the firewall kernel dropping the multicast traffic.
Once I added the Loki host to rule 1 as the source in policy, it could then take over master again.
Important notes:
-When configuring VRRP, be very careful that the security rules are setup correctly.
-When firewall policies are unloaded, IP forwarding is disabled on the system, so if an attack were to happen, it will not route traffic.
Sources: http://louwrentius.com/configuring-attacking-and-securing-vrrp-on-linux.html
Kristen Norris
Awesome.



