Security,Services
SP 800-53rev5 Document Deep Dive
The National Institute of Standards and Technology Special Publication SP 800-53rev5: Security and...
Read more
Security,Secure Access Service Edge,sse
Should You Consolidate Security to Protect Your Hybrid Workforce?
In today's fast-changing world of hybrid networks and workforces, companies are at a pivotal moment...
Read more
Security
2022 Cyber Security Predictions
2021 has been quite the year with the latest Log4j vulnerability as the cherry on top. Our...
Read more
Cybersecurity,Security,Security Awareness
Is this Critical Mistake Hurting Your Cybersecurity Risk Posture?
One of the great ironies of IT is that so many IT and security departments are built on two basic...
Read more
Security
Meet XDR: A New Approach to Threat Detection and Response
You’ve probably heard about it. Maybe you wrote it off as just another product on your...
Read more
Security Control,Cybersecurity,Cyber Threats,Security
Five Critical Steps for an Effective Remote Training Strategy
Cybercrime has skyrocketed during the pandemic, as untrained remote workers adapt to new...
Read more
Vulnerabilities,Cybersecurity,Security
Reopening After COVID-19: Looking Back and Strategies Moving Forward
Businesses are eager to open their doors, many remote workers are ecstatic about it, but reopening...
Read more
Vulnerabilities,Cybersecurity,Cyber Threats,Security,Security Awareness
A Pen Testing Expert Shares the Secret Ways He Gains Access to Businesses
Steve Stasiukonis’ company, Secure Network Technologies, does all kinds of pen testing. When we say...
Read more
Vulnerabilities,Cyber Threats,Security,Security Awareness
The Biggest Threats to Businesses from a Pen Testing Expert
Steve Stasiukonis started doing pen testing professionally in 1997, when a former classmate of his...
Read more
Cyber Threats,Security,Security Awareness,remote work
Little-known Facts About Remote Worker Security that Could Damage Your Business
With the ongoing rush to transition staff to remote workers, great opportunities open for con...
Read more
Vulnerabilities,Cybersecurity,Security,Security Awareness
5 Cyber Security Recaps from the Past Decade—And 5 Predictions for the Next One
While there's a heated debate about whether a new decade is actually beginning, the beginning of a...
Read more
Security Control,Cybersecurity,Security
5 Factors to Make Your Secure Cloud Migration a Success
As more businesses transition their infrastructure to the cloud, understanding how to securely...
Read more
Security Control,Cybersecurity,Security
10 Reasons a vCISO May Be a Good Choice for Your Company
If your company is like most, you’ve grappled with the high cost of a Chief Information Security...
Read more
Security Control,Cybersecurity,Security
SOAR in the Cloud: 7 Factors to Consider
As cybercrime increases, it’s impossible for employees to keep up with every threat. It’s crucial...
Read more
Cybersecurity,Cyber Threats,Security,Security Awareness
A Former CTO of the FBI Cyber Division on the State of Cybersecurity
Part 3 of a three-part series Milan Patel, current chief client officer at BlueVoyant and former...
Read more
Cybersecurity,Cyber Threats,Security
The Advice a Former CTO of the FBI Cyber Division Would Give His Best Friend About Cybersecurity
Milan Patel has seen a thing or two. He can’t talk about some of it, which makes sense, given that...
Read more
Cybersecurity,Cyber Threats,Security
What a Former CTO of the FBI Cyber Division Thinks Should Keep You Up At Night
Part 1 of a three-part series Even if you weren’t interested in cybersecurity, Milan Patel is the...
Read more
Security,Security Awareness
9 Questions You Should Ask When Considering Cloud-Based Tech
To paraphrase Zoolander, cloud-based technology is so hot right now. There are good reasons for...
Read more
Cybersecurity,Cyber Threats,Security,Security Awareness
How to Improve Your IT Security for the Upcoming Elections
Small governments seem to be stuck between a rock and several hard places.
Read more
Cybersecurity,Security,Security Awareness
New Tools to Protect Credit Cards at Gas Stations But Who Gets to Use Them?
If you live in the U.S. and have ever noticed false charges on your credit card statement and had...
Read more
Cyber Threats,Security,Security Awareness
If Your Healthcare Data is Leaked Chances are Your Doctor’s Office, not an Evil Hacker, is to Blame
New research from Michigan State and Johns Hopkins Universities show that failed internal...
Read more
Cybersecurity,Security,Security Awareness
New Advances Show Evil Hackers can use Cell Phone Apps to Capture your Information by Sound
Evil hackers and corporate spies have had the ability to record the loud tap-tap-tap of computer...
Read more
Cybersecurity,Cyber Threats,Security
Research Suggests Your Battery Might be the Key to Thwarting the World’s Most Elusive Malware
Micro-architectural attacks are arguably the most dangerous and difficult of all forms of systems...
Read more
Vulnerabilities,Security Control,Security,Security Awareness
5 Mistakes Made In the Capital One Breach and How to Avoid Them
If an amateur hacker could bring down a Fortune 500 company, how can your company hope to avoid the...
Read more
Cybersecurity,Security
How Manufacturers Can Protect Against Ransomware Attacks
You might think your company doesn’t have much in common with the largest shipping company in the...
Read more
Security
5 Starter Questions to Keep Your Smart Devices Secure
As the popularity of “smart homes” increases, new research continues to find concerns about the use...
Read more
Security,Security Awareness
What Data Breaches and the Notre Dame Cathedral Fire Have in Common
On April 15, 2019, a flame ignited Notre Dame Cathedral in Paris and many watched as roughly 500...
Read more
Vulnerabilities,Cybersecurity,Security,Security Awareness
5 Lesser Known Impacts of Poor Security
You wouldn’t leave the doors to your business unlocked, would you? Of course you wouldn’t. In the...
Read more
Security
5 Questions You Should Ask to Ensure You’re Approaching Data Security Correctly
Industries are transforming with the help of digital technologies and IT, and as competition...
Read more
Security
The Shadow Cloud Knows
Author: Tim O'Connor You may have heard of “Shadow IT”. Shadow IT is the term that describes when...
Read more
Security
If your company experiences an information security breach, will customers order from you again?
Author: Tim O'Connor New psychological studies could be a game changer. Damage to reputation and...
Read more
Security
Why Security Won’t be the Reason You Succeed, but may be the Reason You Fail
At Cadre, we like to say that security isn’t the reason your company succeeds, but it could be the...
Read more
Security,Security Awareness
5 Ways to be Sure You’re not Over- or Under-Solving for Security
Remember the story of Goldilocks breaking into the three bears’ cottage and wreaking havoc?...
Read more
Security,Security Awareness
Why the Citrix Breach Happened and 6 Steps You Can Take to Protect Your Company
What happened? Citrix, an American software company, disclosed a security breach in which hackers...
Read more
Security
Did we miss China’s Quantum Sputnik?
Author: Tim O'Connor On October 4, 1957 the Sputnik 1 satellite woke up the world and launched (pun...
Read more
Security
Common Security Assessment Questions
Penetration tests and network vulnerability assessments are essential components to a company's...
Read more
Security
Malware-as-a-Service Empowers Cyber Attackers
Cyber crime is now democratized. In today’s cyber threat landscape, launching a cyber attack is no...
Read more
Security
8 Steps to Prevent the Next Data Breach
Sensitive data is being exposed at an alarming rate due to unwanted data breaches. Is your business...
Read more
Security
Benefits of Moving to the Cloud
Almost every organization has moved at least part of their operation to the cloud. You can’t browse...
Read more
Security
How IaaS (Infrastructure as a service) can cut down your IT spend
IaaS is the first tier of a triad of outsourced cloud services. The top two are PaaS (platform as a...
Read more
Security
Encryption Methods in the Cloud
If you’re going to fly with the eagles in the cloud, you need to be grounded in the best cloud...
Read more
Security
Three Wrong Assumptions Business Owners Have About Cloud Security
Moving data and other company solutions to the cloud can pay off in significant ways for...
Read more
Security
How to know if your Facebook Account has been Breached
Watch this video to determine if your Facebook Account has been compromised:
Read more
Security
If you think Iranian and Russian disinformation memes are designed to change people’s minds and opinions, you might already be deceived!
Author: Tim O'Connor Let me begin by saying I am not an expert on Iranian and Russian...
Read more
Security
Talk About Cloud First or Get There Last
By: Phil Swaim There is no doubt one of the greatest innovations in IT of the last 10 years has...
Read more
Security
Internal use of SSL/TLS: Risks, Challenges, and Opportunities for Further Consideration
SSL is a ubiquitous technology introduced in 1994. The use of SSL, and it’s descendant, TLS, is...
Read more
Security
Your ISP Potentially Knows EVERYTHING that you do through your Internet Connection
Q. Who knows more about your internet use then Facebook, Amazon or even your browser? A. Your ISP...
Read more
Security
HID Proximity Access Cards: Unsafe at Any Speed!
Many workers are familiar with the venerable HID access card. You present the card to a badge...
Read more
Security
How to Encourage Your Team to use Stronger Passwords
If you work in any sort of IT/cyber security role, you know it’s imperative to be concerned with...
Read more
Security
What is Malware?
Malware is a portmanteau of "malicious" and "software". As the name implies, malware is created...
Read more
Security
Understanding Password Manager’s Risks and Rewards
These last several weeks have brought up a lot of interesting discussions around passwords and...
Read more
Security
When a Technology Becomes a Security Control
As a Chief Information Security Officer (CISO) or Information Security manager, you have to make...
Read more
Security
Small Vulnerabilities Can Lead To Catastrophic Results [Part 2]
Not all leaks are the result of malice. In 2006, America On-Line (AOL) negligently published 20...
Read more
Security
Small Vulnerabilities can lead to Catastrophic Results [part 1]
When it comes to security, most IT departments focus primarily on network and application security....
Read more
Security
It’s Not Fear Factor, it’s Multi-Factor
What is multi-factor authentication? Multi-Factor Authentication (MFA) is a method used to grant...
Read more
Security
Encoding, Hashing, and Encryption: What’s the difference?
Encoding, hashing, and encrypting are common concepts applied and discussed when trying to secure...
Read more
Security
Your Single Source for Security Guidance
Your network is important to you and it's critically important to us. Does alignment of business,...
Read more
Security
Inspecting Encrypted Network Traffic
Encrypted traffic is becoming increasingly prevalent on corporate networks.
Read more
Security
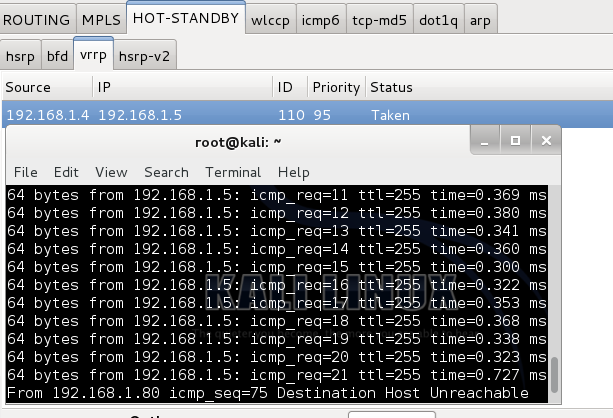
Taking Over Master Membership and Securing VRRP
Topology: Part 1 (No Firewall Module) Instructions for setup are in the link above. You must...
Read more
Security
Breach Mitigation: Will It Take a Village?
No one is immune from data breaches. We’ve witnessed department stores, hospitals, insurance...
Read more