Vulnerabilities,Cybersecurity,Cyber Threats,Security,Security Awareness
A Pen Testing Expert Shares the Secret Ways He Gains Access to Businesses
Steve Stasiukonis’ company, Secure Network Technologies, does all kinds of pen testing. When we say...
Read more
Vulnerabilities,Cyber Threats,Security,Security Awareness
The Biggest Threats to Businesses from a Pen Testing Expert
Steve Stasiukonis started doing pen testing professionally in 1997, when a former classmate of his...
Read more
Cybersecurity,Security Awareness
How to Enable Your Employees to Work Remotely Without Compromising Security
With the current economic and social uncertainty in today’s landscape and the rush to transition...
Read more
Security Awareness,remote work
How to Transition to Working Remotely During a Crisis
Jim Hebler has worked in cybersecurity for nearly 18 years. He started out covering technology as a...
Read more
Cybersecurity,Cyber Threats,Security,Security Awareness
A Former CTO of the FBI Cyber Division on the State of Cybersecurity
Part 3 of a three-part series Milan Patel, current chief client officer at BlueVoyant and former...
Read more
Cybersecurity,Cyber Threats,Security
The Advice a Former CTO of the FBI Cyber Division Would Give His Best Friend About Cybersecurity
Milan Patel has seen a thing or two. He can’t talk about some of it, which makes sense, given that...
Read more
Cybersecurity,Cyber Threats,Security
What a Former CTO of the FBI Cyber Division Thinks Should Keep You Up At Night
Part 1 of a three-part series Even if you weren’t interested in cybersecurity, Milan Patel is the...
Read more
Cybersecurity,Security
How Manufacturers Can Protect Against Ransomware Attacks
You might think your company doesn’t have much in common with the largest shipping company in the...
Read more
Security,Security Awareness
What Data Breaches and the Notre Dame Cathedral Fire Have in Common
On April 15, 2019, a flame ignited Notre Dame Cathedral in Paris and many watched as roughly 500...
Read more
Security
5 Questions You Should Ask to Ensure You’re Approaching Data Security Correctly
Industries are transforming with the help of digital technologies and IT, and as competition...
Read more
Security
If your company experiences an information security breach, will customers order from you again?
Author: Tim O'Connor New psychological studies could be a game changer. Damage to reputation and...
Read more
Security
Common Security Assessment Questions
Penetration tests and network vulnerability assessments are essential components to a company's...
Read more
2019 Cyber Attack Trends
In 2018, threat actors consistently improved their cyber weapons, quickly adopted new methods and...
Read more
Security
Malware-as-a-Service Empowers Cyber Attackers
Cyber crime is now democratized. In today’s cyber threat landscape, launching a cyber attack is no...
Read more
Security
8 Steps to Prevent the Next Data Breach
Sensitive data is being exposed at an alarming rate due to unwanted data breaches. Is your business...
Read more
Security
Benefits of Moving to the Cloud
Almost every organization has moved at least part of their operation to the cloud. You can’t browse...
Read more
Security
How IaaS (Infrastructure as a service) can cut down your IT spend
IaaS is the first tier of a triad of outsourced cloud services. The top two are PaaS (platform as a...
Read more
Security
Encryption Methods in the Cloud
If you’re going to fly with the eagles in the cloud, you need to be grounded in the best cloud...
Read more
Security
Three Wrong Assumptions Business Owners Have About Cloud Security
Moving data and other company solutions to the cloud can pay off in significant ways for...
Read more
Security Awareness
How to Create an Effective Security Awareness Program
"Social engineering bypasses all technologies, including firewalls." -Kevin Mitnick Social...
Read more
Security
How to know if your Facebook Account has been Breached
Watch this video to determine if your Facebook Account has been compromised:
Read more
GRC
GRC Roadmap Webinar
In this webinar we discuss what GRC is, why you need a GRC Strategy Roadmap, and how you can...
Read more
Events
Cadre Information Security is hosting a Happy Hour at The District Tap in Indianapolis
Ready for a nice cold beverage? Join us on Thursday, March 1st at The District Tap to meet our...
Read more
Services
Cadre's Digital Training Classroom
Cadre’s new upgraded classroom brings better than state-of-the-art security training for students...
Read more
Services
Benefits of a Virtual Chief Information Security Officer Service (vCISO)
By now you are probably aware of the advantages of using a virtual computer (VM) and how that...
Read more
Security Awareness
Security Awareness Evaluation - Don't Fall for the "Streetlight Effect!"
A policeman sees a drunk man searching for something under a streetlight and asks what the drunk...
Read more
Services
Cadre Now Offers Managed Services
When it comes to managing IT for your business, you can never have too much help. That's why Cadre...
Read more
Services
Monitor the Security State of your Internal Network with Virtual Network Vulnerability Scanning
Keeping abreast of your network and infrastructure can be a daunting task. Vulnerabilities are much...
Read more
GRC
What is GRC?
GRC stands for Governance, Risk and Compliance. The Open Compliance and Ethics Group (OCEG) has...
Read more
Events
InfoSec Summit SSW-2017 Cleveland Ohio
Cadre Information Security is proud to be a sponsor and exhibitor at the Security Summit in...
Read more
Events
Data Connectors - Nashville
Cadre Information Security is proud to be a sponsor and exhibitor at the Data Connectors in...
Read more
Events
SecureWorld Cincinnati
Cadre Information Security is proud to be a sponsor and exhibitor at the SecureWorld Cincinnati.
Read more
Security
How to Encourage Your Team to use Stronger Passwords
If you work in any sort of IT/cyber security role, you know it’s imperative to be concerned with...
Read more
Security
What is Malware?
Malware is a portmanteau of "malicious" and "software". As the name implies, malware is created...
Read more
About Cadre
What is a value-added reseller?
A value-added reseller (VAR) is a company that takes an existing product and adds extra features...
Read more
Security
Understanding Password Manager’s Risks and Rewards
These last several weeks have brought up a lot of interesting discussions around passwords and...
Read more
Security
When a Technology Becomes a Security Control
As a Chief Information Security Officer (CISO) or Information Security manager, you have to make...
Read more
Security
Small Vulnerabilities Can Lead To Catastrophic Results [Part 2]
Not all leaks are the result of malice. In 2006, America On-Line (AOL) negligently published 20...
Read more
Security
Small Vulnerabilities can lead to Catastrophic Results [part 1]
When it comes to security, most IT departments focus primarily on network and application security....
Read more
Security
It’s Not Fear Factor, it’s Multi-Factor
What is multi-factor authentication? Multi-Factor Authentication (MFA) is a method used to grant...
Read more
Services
5 Major Benefits of Security Assessments
Security assessments should be a part of any company’s security program. At a high level, they...
Read more
Security
Encoding, Hashing, and Encryption: What’s the difference?
Encoding, hashing, and encrypting are common concepts applied and discussed when trying to secure...
Read more
Security
Your Single Source for Security Guidance
Your network is important to you and it's critically important to us. Does alignment of business,...
Read more
Security
Inspecting Encrypted Network Traffic
Encrypted traffic is becoming increasingly prevalent on corporate networks.
Read more
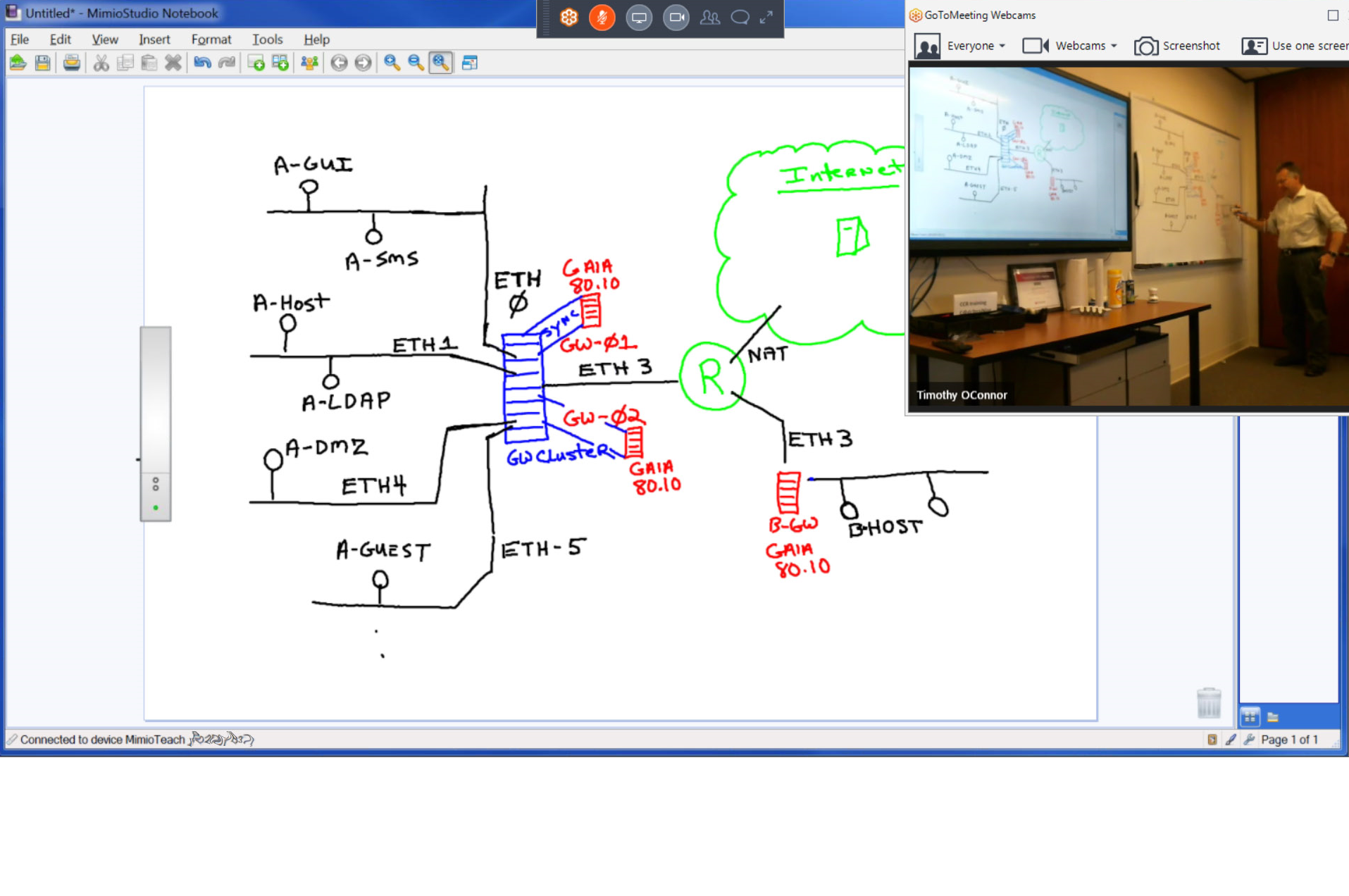
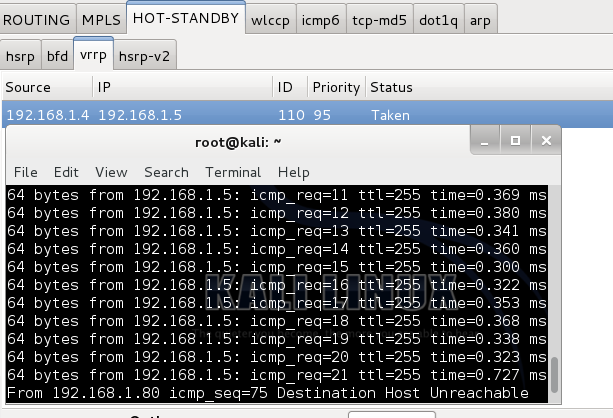
Security
Taking Over Master Membership and Securing VRRP
Topology: Part 1 (No Firewall Module) Instructions for setup are in the link above. You must...
Read more
Security
Breach Mitigation: Will It Take a Village?
No one is immune from data breaches. We’ve witnessed department stores, hospitals, insurance...
Read more
About Cadre
Cadre's Story
Very few people were talking about network security when Cadre was formed back in late 1991. By...
Read more