Security Awareness
The Worst Things to Share on Social Media
As a business professional, why should you care what your employees post on social media?
Even before COVID-19 caused the mass migration to a remote workforce, many successful hacks into organizations originated from an employee’s personal device (cell phone, tablet or laptop) or from information leaked from a personal social media account. I am NOT suggesting that organizations play “big brother” and attempt to police the personal affairs of employees online, but I am going to make a case for education, awareness and due care.
With the current increase of remote workers, the danger of ransomware or other kinds of malware and attacks caused by user-actions has increased exponentially. We covered some of these dangers in these past articles.
Read Little-Known Facts About Remote Worker Security that Could Damage Your Business
While we can’t (and should not want to) dictate what our employees share about their personal lives on social media, we also can’t escape the fact that poor social media “hygiene” is a risk to the organization. Employees will forward emails between work and home accounts and use similar passwords for personal accounts and work accounts.
The most effective way to mitigate the risk of users “taking malware to work” is a good Security Awareness Program designed with the help of a trusted advisor. In this article we are going to cover a few of the worst kinds of behavior that your employees will hopefully avoid, once they receive proper training. When sharing this information it is critical to let the employees know that good social media hygiene helps protect not just the organization but also themselves, family, and friends. You may wish to convey the information in this article to your staff and partners.
The 4 Worst Forms of Social Media Hygiene
Just as you would not wish to come into the office with halitosis, stained clothes, toilet paper on your shoe, a sprig of broccoli in your teeth or smelling like the corner bar, there are some basic social media hygiene behaviors that can help you and your families stay out of the gutter. Avoiding these simple kinds of social media posts will not only show you have a good character but will also greatly reduce the chances of you or your friends being hacked.
It’s All Fun and Games Until Someone Gets Hacked
Games are fun and one of the attractions of social media is sharing personal trivia with friends and family. I am not going to ask you to stop playing games, but it is important to recognize that some of the games on social media have been designed by evil hackers.
Many of these games look innocent and don’t SEEM to give away any information to hackers, but hackers are a crafty lot. Many of these games, like the popular “what is your elf name”, ask for your birthdate or a part of your name as part of the process. Others ask about your favorite pet or your phone number. What could be wrong with these games?
The way it works is that evil hackers simply reverse your post to find out pieces of your birthday, phone number and/or favorite things (people often use favorite things like pet names as passwords). After you answer one or more of these quizzes, enough of a profile is built to allow the evil hacker to guess likely passwords or forms of authentication such as the last digits of your phone number. With this information, for instance, they could steal your pharmacy prescription:
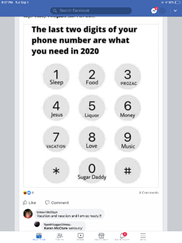
A legitimate question upon seeing the hackers game shown here is, “why would knowing only the last two digits of my phone number be a risk?” The answer is that knowing this is a gold mind to a mentalist or an evil hacker as this reduces the possible remaining numbers to a manageable sum. The evil hacker can use another game or source to get the other digits or might just use them to CONFIRM other information that can be found publicly as they build a profile on you. In the social media post above, we found people even offering up remaining digits as part of the fun of the game. You can find out more about the “Elf Name” hacks and the relationship of mentalism to Social Engineering here.
What is Amen farming and what harm could it possibly do?

“Amen Farming” also known as “Like Farming” is a social media hack that tries to compel people to quickly post a one word comment about a compelling subject. On the surface it would seem that this is no different then sharing any other meme and making a comment. It turns out on further examination though that this is a powerful psychological tool that can exploit the privacy settings of respondents.
As a security professional I am extremely fascinated by the many ways Amen Farming can be exploited. I ALMOST don’t want to warn my friends just so that I can track the methodology of the hack. There are almost a dozen ways these posts can assist evil social media hackers. The first is that many more people will respond to these one-word memes than would respond to a regular discussion. When a long chain of shares and comments are built, this allows the original posting account to mine information from the replies that would normally be blocked by privacy settings. We don’t know all the ways this information can help evil hackers but we do know it assists them in profiling accounts and building up the reputation of an account that they will later use for friend invites and misinformation campaigns.
This practice has become such a gold mine for evil hackers that they often don’t even bother to make up their own memes. They just find a popular one and photoshop “say amen” or another phrase into the meme graphic as in this example.
The best thing to do is to NOT SHARE these memes and of course don’t type “amen”. When you see someone sharing these kinds of memes let them know it might be a scam and point them to this article or the one from “That’s Nonsense”: (https://www.thatsnonsense.com/facebook-like-share-photo-scams-dont-make-scammers-rich/).
If you MUST share the meme, don’t share it from the original account. Download the graphic and then reshare it as your own content and also make sure your social media privacy settings are set to “friends only”.
Fact Checking Hoaxes
If you are reading this article I suspect you already know that spreading hoaxes on social media is a bad thing and should be avoided. Therefore, I won’t be going into much detail but I would be remiss if I did not include this in our list.
An interesting new development in the “fake news” wars is that scammers are now doing their best to discredit fact checking outlets. This makes perfect sense as the ploy to “shoot the messenger” goes back long before social media. You should not take the word of a fact checker, until you verify the contents of the article and the sources used for fact-checking. While statistics show only a very small number of fact checking articles from well known sites ‘get it wrong,’ it still can happen. In practice, however, it seems hard to get your crazy uncle to do ANY fact checking much less use additional due diligence. For yourself, some fact checking is better than none and I would urge you to read the entire write up from the fact checker.
If your crazy uncle does not believe any fact checkers, try going to the sources in the fact checker article and posting those directly.
“Watch Out For This Hacker” Warnings
Several times a year instant messaging hacks show up warning people to not befriend some ‘famous’ evil hacker. A recent example is the “friend request from Jayden K. Smith” hoax. Since Jayden K. Smith is not a real person and she won’t actually send anyone a friend request, what is the harm?
The harm from these kinds of messaging scams is similar in some ways to Amen Farming. The evil hackers are building profiles and networks and as a side they are helping to muddy the water and discredit real notifications about social engineering. The principle difference is the media used, in this case, instant messaging services.
Accidental Information Leakage in Social Media
Never post your phone number, address, age or passwords on social media. While I think most of us know that, you should know that this information can easily be shared inadvertently, often through photos.
A good example happened last year when a photo of a government emergency worker was posted but on the monitor behind him was a post-it note with a government network password.
Now that many of us are working from home, this kind of information leakage becomes much more common. Check to make sure any photos you post do not include shots of the desk were papers might be in sight or calendars on the wall. When you post a photo of that new item that just arrived in the mail, l can you see your mailing address?
Screenshots are particularly dangerous and should be examined and edited closely before sharing. Many people now use multiple monitors at home and don’t realize that a screen shot includes BOTH screens. Screen shots from phones and tablets are also possible sources of information leakage.
Knowledge is Power
I hope this article has helped you to become aware of some of the top common exploits that happen with social media sharing and that you will pass this information on to others.
If your organization would like help in developing policies, Security Awareness Programs or other related issues please let us know. We have lots of services, workshops, webinars and direct help for you.