Quantum Computing
The Quantum Computer Security Risks You Likely Haven’t Heard About
You’ve almost certainly heard about the security issues that will arise when quantum computers are...
Read more
UPDATE: Michigan law banning VPNs and Post-Quantum VPN Encryption
Lots has been happening in VPN-land over the past couple of weeks. If your time is short, here are...
Read more
The Truth About VPNs and the Rise of Quantum Decryption
During Risk Assessments, and working with clients, I routinely run into situations where users...
Read more
vciso,assessment
Risk Assessment, Vulnerability Assessment and Pen Testing
Why are they so confusing, and what you need to know! Almost weekly, a customer contacts me asking...
Read more
Cybersecurity,Services
As CISA downsizes, what can we do for support and guidance?
CISA (Cybersecurity and Infrastructure Security Agency) is the nation's cyber security defense...
Read more
Cybersecurity,Security Awareness,Internet of Things,multifactor authentication,MFA
Authentication vs. Privacy
Like many “teeter-totter” issues, there is a give-take relationship between new authentication...
Read more
Security budget
Why Medium-sized Companies Waste 80% of Their IT Security Budget
In 2008 I was involved in a research project that looked at the effectiveness of training IT...
Read more
Security Awareness
New Scam Alert + Easy to Share Information for Employees
For Security Awareness to be effective, it has to be a continuous effort based on current threats....
Read more
The Biggest Security Awareness Misconceptions – Part 2
In part one of this blog, we reviewed the most common Security Awareness misconceptions, revealed...
Read more
Security Awareness
The Biggest Security Awareness Misconceptions – Part 1
There’s a conversation that has been playing on repeat about Security Awareness. It usually goes...
Read more
Cybersecurity,Services
How to Choose a Security Training Course
It’s undeniable—security training, whether on practices or products, is chock full of benefits....
Read more
Services
NEW Check Point Classes & Updates
As a Check Point Platinum Elite training partner, the team at Cadre is always working behind the...
Read more
Security Awareness
How to Develop an Effective Security Awareness Program
Security Awareness is well known for being the “best bang for the buck” out of all the risk...
Read more
Security Awareness
The Worst Things to Share on Social Media
As a business professional, why should you care what your employees post on social media? Even...
Read more
Security Awareness,smartphone security
The Latest Smart Phone Hacking Update
New security concern: Malware that can copy all the physical keys on your keychain!
Read more
Cyber Threats,Security,Security Awareness,remote work
Little-known Facts About Remote Worker Security that Could Damage Your Business
With the ongoing rush to transition staff to remote workers, great opportunities open for con...
Read more
Cybersecurity,Cyber Threats,Security Awareness
Five Tips to Ensure Your Company's Bluetooth Security Policies are Up to Date
Urban Legend Becomes Real Several years ago some reports came to information security experts from...
Read more
Security Control,Cybersecurity,Cyber Threats
6 Questions to Help You Hire & Evaluate Security Solution Providers
Cybercrime cost the global economy as much as $600 billion in 2017,(1) so unless your business and...
Read more
Insider,Cybersecurity,Cyber Threats
An Insider's Guide to the FBI Cyber Security Briefing on Iran
Cadre’s manager of Knowledge Services, Tim O’Connor, was invited to an FBI Cyber Security briefing...
Read more
Security Control,Cybersecurity,Security Awareness
The Fact and Fiction of the Business Risks Posed by IOT Devices
A casino hacked through an aquarium heater* sounds like fiction—but this recent headline news was...
Read more
Cybersecurity,Cyber Threats,Security Awareness
Myth Busted: Small Organizations are at Low Risk of Hacking Because they are not Desirable Targets For Hackers
All of these are common myths, but only one has dangerous misinformation. Can you figure it out?...
Read more
Security,Security Awareness
9 Questions You Should Ask When Considering Cloud-Based Tech
To paraphrase Zoolander, cloud-based technology is so hot right now. There are good reasons for...
Read more
Cybersecurity,Cyber Threats,Security,Security Awareness
How to Improve Your IT Security for the Upcoming Elections
Small governments seem to be stuck between a rock and several hard places.
Read more
Cybersecurity,Security,Security Awareness
New Tools to Protect Credit Cards at Gas Stations But Who Gets to Use Them?
If you live in the U.S. and have ever noticed false charges on your credit card statement and had...
Read more
Cyber Threats,Security,Security Awareness
If Your Healthcare Data is Leaked Chances are Your Doctor’s Office, not an Evil Hacker, is to Blame
New research from Michigan State and Johns Hopkins Universities show that failed internal...
Read more
Cybersecurity,Security,Security Awareness
New Advances Show Evil Hackers can use Cell Phone Apps to Capture your Information by Sound
Evil hackers and corporate spies have had the ability to record the loud tap-tap-tap of computer...
Read more
Cybersecurity,Cyber Threats,Security
Research Suggests Your Battery Might be the Key to Thwarting the World’s Most Elusive Malware
Micro-architectural attacks are arguably the most dangerous and difficult of all forms of systems...
Read more
Vulnerabilities,Security Control,Security,Security Awareness
5 Mistakes Made In the Capital One Breach and How to Avoid Them
If an amateur hacker could bring down a Fortune 500 company, how can your company hope to avoid the...
Read more
Security
5 Starter Questions to Keep Your Smart Devices Secure
As the popularity of “smart homes” increases, new research continues to find concerns about the use...
Read more
Vulnerabilities,Cybersecurity,Security,Security Awareness
5 Lesser Known Impacts of Poor Security
You wouldn’t leave the doors to your business unlocked, would you? Of course you wouldn’t. In the...
Read more
Surprise on the Dark Web Underscores Need to Understand Security Technology
Author: Tim O'Connor Impersonation, often called “spoofing” in information security lingo, is one...
Read more
Vulnerabilities,Security Control,Cybersecurity,Security Awareness
Security Trends and Takeaways for the Second Half of 2019
So much has happened in terms of information security and breaches in 2018 that it can be a little...
Read more
Security
The Shadow Cloud Knows
Author: Tim O'Connor You may have heard of “Shadow IT”. Shadow IT is the term that describes when...
Read more
New Research Finds Flaws in Perceived Cyber Security; Visual Clues Sometimes Help
Author: Tim O'Connor Encouraging employees to improve their security hygiene can feel like an...
Read more
Security
Why Security Won’t be the Reason You Succeed, but may be the Reason You Fail
At Cadre, we like to say that security isn’t the reason your company succeeds, but it could be the...
Read more
Security,Security Awareness
5 Ways to be Sure You’re not Over- or Under-Solving for Security
Remember the story of Goldilocks breaking into the three bears’ cottage and wreaking havoc?...
Read more
Cyber Threats,Security Awareness
Grab-n-Go Baldr Malware: A Stunning New Type of Malware
A revolutionary new type of malware toolset is starting to show up in dark web hacking forums. The...
Read more
Security,Security Awareness
Why the Citrix Breach Happened and 6 Steps You Can Take to Protect Your Company
What happened? Citrix, an American software company, disclosed a security breach in which hackers...
Read more
Security
Did we miss China’s Quantum Sputnik?
Author: Tim O'Connor On October 4, 1957 the Sputnik 1 satellite woke up the world and launched (pun...
Read more
Security Awareness
Security Awareness Training FAQs
We receive a number of questions regarding security awareness training. Below are some common...
Read more
Security Awareness
5 Things to keep in mind when Implementing a Security Awareness Program
What are the 5 most important things to keep in mind when implementing a security awareness...
Read more
Security Awareness
Cadre’s Security Awareness Services Meet Requirements for Major Compliance Standards
Cadre’s Security Awareness class, course design and consulting services are now able to meet...
Read more
Honoring the Code Talker, Alfred Newman
Author: Tim O'Connor This piece is honoring the hero, Alfred Newman. Alfred Newman passed away...
Read more
Security
If you think Iranian and Russian disinformation memes are designed to change people’s minds and opinions, you might already be deceived!
Author: Tim O'Connor Let me begin by saying I am not an expert on Iranian and Russian...
Read more
Security
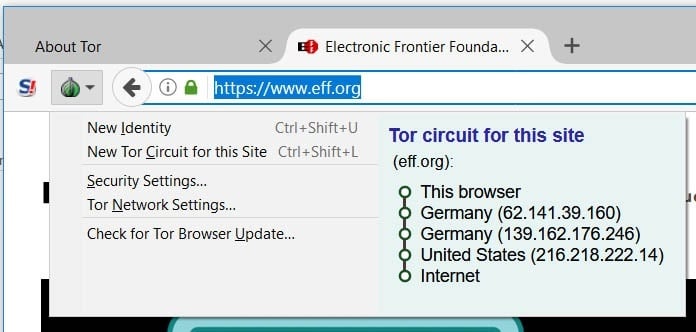
Your ISP Potentially Knows EVERYTHING that you do through your Internet Connection
Q. Who knows more about your internet use then Facebook, Amazon or even your browser? A. Your ISP...
Read more
Security Awareness
How to Legally Practice Social Engineering
Social Engineering is without question the most powerful and successful hacker skill of all time,...
Read more
Security Awareness
Should we Fear the Amazon Echo or Other Smart Speakers in our Home?
Author: Tim O’Connor I am a cyber security professional and when I tell some of my peers that I...
Read more

.jpg)